capabilities
Solutions built at the speed of inspiration.
Innovation requires investment and Technica devotes significant resources to support our own Independent Research and Development Lab, providing technical vision three or more years into the future. We are dedicated to pragmatic and holistic approaches to problem solving that are nimble enough to respond to ever-changing client needs.
Continuous Innovation Model
our expertise
No matter the problem, we have the experience to help.
ai / machine learning
Technica has developed and leveraged a variety of machine learning algorithms—including deep learning/neural networks—on a spectrum of computing platforms to perform complex tasks like image recognition, anomaly detection, and time-series analysis. Probably no other technology will have a bigger impact on IT than AI in the next decade.
data analytics
Technica employs next-generation architectures and methods to derive meaning and value from massive datasets. Our solutions incorporate and integrate closed open source products. Technica developed IP for best-of-breed analytic insight. We utilize next-generation methods to derive meaning from datasets that are too large for traditional databases.
cyberspace operations
Technica has in-depth knowledge of cyberspace operations and has operated some of the Federal Government’s largest networks. We integrate defensive cyber operations with network operations which leverages the power of analytics and machine learning to effectively and autonomously secure, operate, and defend our nation’s Information Technology.
ai acceleration
Capitalizing on the benefits of parallel processing to dramatically improve total application performance and increase solution affordability and scalability. The parallel programming capabilities offered by GPUs is a game-changer, especially in AI and ML.
Professional services
We evaluate emerging technologies to deliver exceptional solutions.
data
Data Integration and Automation, Data Cleansing, Data Generating Algorithms, Big Data Analytics, Deep Learning, Machine Learning, Data Science, Artificial Intelligence, Tactical Edge AI Algorithms’
applications
Agile Development, DevSecOps, App Modernization/Migration, Microservices and Containerization, AI,/Cognitive Discovery, AI App Solutions
infrastructure
AIOPS, Enterprise Service Management, Enterprise Architecture, Visualization & Analysis, Network Engineering, Continuity of Operations/Disaster Recovery, Defensive Cybersecurity AI Algorithms
AIOps
Unique solutions for unique organizations.
What is aIOPs?
AIOPS is the application of Artificial Intelligence and Machine Learning for autonomous IT and mission operations.
What can it do?
Makes Sense of Data
Derives Insights from Data
Predicts & Prevents Incidents
Automates Remediation
Continuous Compliance
How does it work?
Machine learning leverages algorithms and data to train models. These models are used to provide insights and automation.
1. Forming Data Base
- Siloed data
- Real-time data
- Historical data
- Contextualization and correlation
2. Data Platform
- Data Sets are ingested by the data platform
4. Insights/Foresights
- Root cause determination
- Prediction and prevention
- Surface signals
3. AI Machine Learning
- Pattern discovery
- Anomaly detection
5. Cognitive Automation
- Dynamic context-based triage
- Closed-loop self-healing
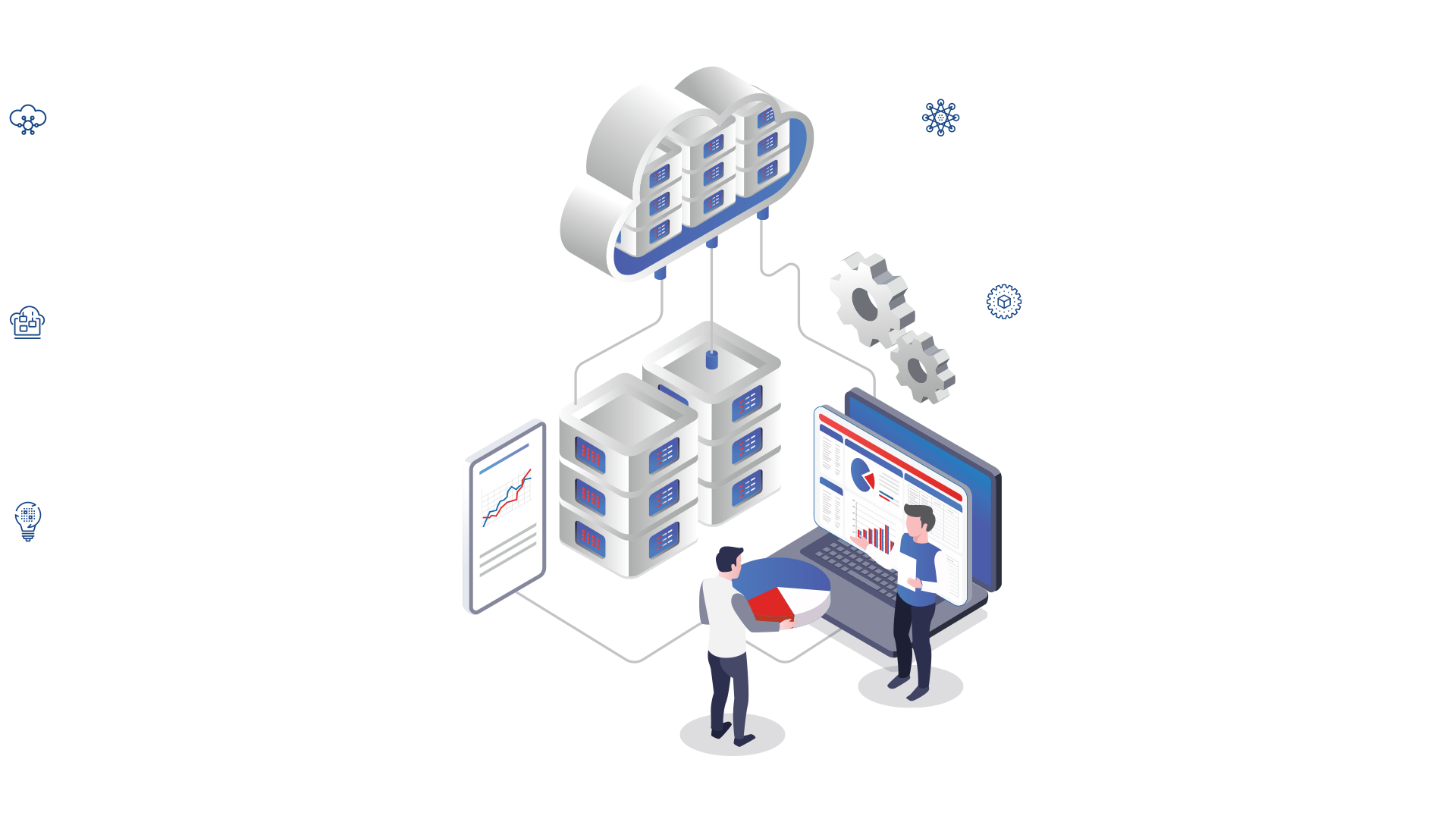
How can it benefit Mission Operations?
AIOPS transforms your enterprise from slow and reactive to agile and proactive extending beyond the realms of IT into mission operations.
Speed Up Investigations
Identify vulnerabilities, trends, and pinpoint root causes through analytics and automation.
Streamline Monitoring
Unified visibility into health, status, and security posture of services, apps, physical, virtual, and cloud infrastructure.
Actionable Insights
Analytic insights eliminate the noise and help focus attention on what's important for faster remediation.
Increase Productivity
Smart collaboration, agile data fabric, orchestration, predictive optimization, and intelligent automation.
Mission Solutions
We’ve worked for many different agencies since our inception and
served as a trusted advisors while providing our innovative
technology solutions for an array of problems.